Beware iOS users: malware is by no means an Android-only problem
 There’s a common misconception that we’ve taken note of. It is a widely believed sentiment, one that is thought to be a calming reassurance, that “Malware is an Android-only problem”.
There’s a common misconception that we’ve taken note of. It is a widely believed sentiment, one that is thought to be a calming reassurance, that “Malware is an Android-only problem”.
This statement is completely and utterly false. Those who believe it exposes themselves to a multitude of vulnerabilities that will no doubt be exploited by an opportunistic attacker. Malware is an iOS problem too, let us explain why.
The misconception
This deeply rooted misconception comes from the fact that the Android mobile operating system is inherently more customizable than that of iOS.
Android puts end users in the driver’s seat and allows them to be the creators of their own mobile experience. Apple on the other hand, has a strict set of rules users must adhere to, and allows limited customization of its settings and mobile dashboard.
One of these OSs is not better than the other, it all comes down to user preference. The caveat here is that if the configuration of a device is mismanaged, the device in question is more susceptible to being impacted by a mobile threat.
 Because iOS makes it much more difficult to alter device configuration, Android poses a larger risk to users in making them vulnerable to things like rooting malware attacks (where a hacker attempts to gain administrative privileges to a device).
Because iOS makes it much more difficult to alter device configuration, Android poses a larger risk to users in making them vulnerable to things like rooting malware attacks (where a hacker attempts to gain administrative privileges to a device).
The Android OS gives end users an easily accessible option to allow for third parties to gain administrative rights to the device. These permissions can easily be taken advantage of by an attacker. Gaining these same permissions on an iOS device is a much more difficult feat.
This however, does not mean that iOS is completely safe. In fact, there have been many instances where iOS devices have been affected by highly severe strains of malware.
iOS malware: the facts
iOS devices tend to be well protected against malware thanks to their rigid OS constraints. This of course, doesn’t mean hackers haven’t been up to the challenge.
The following iOS malware variants have affected Apple devices within corporate mobile fleets in the last three years:
AceDeceiver
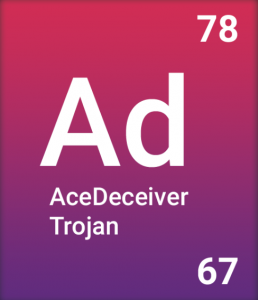 Type: Trojan
Type: Trojan
Severity: 78
Prevalence: 67
AceDeceiver was the name given to a family of trojans found targeting iOS devices. This malware exploits design flaws in Apple’s Digital Rights Management software (DRM) called FairPlay in order to install malicious apps on both iPhones and iPads. FairPlay is the protection mechanism used by Apple to protect copyrighted works sold through the App Store.
Devices don’t have the be jailbroken in order for an AceDeceiver attack to be successful. In fact, the infection vector is very cleverly designed to circumvent the need for a jailbroken device. The malware uses a method known as a “FairPlay Man-in-the-Middle (MitM) attack” in order to install malicious apps on a device.
When any app is installed on an iOS device, the device itself requests an authorization code to prove the app was purchased fairly (this is a FairPlay requirement). This is required as many times, apps are purchased on a user’s computer and installed on a mobile device through the connection to the PC.
In an AceDeceiver attack, a hacker is able to sit in the network between the app purchase and the download to the computer to intercept the authorization code. AceDeceiver can then, via replicating iTunes behaviours from the computer, force the iOS device into downloading any application the attacker so chooses, via replicating iTunes behaviours from the computer.
AceDeceiver has been found to download three unique malicious apps to devices. All three were disguised as ‘wallpaper’ apps and managed to pass Apple’s review process flawlessly. These apps provided a connection to a third party app store and encouraged users to input theirApple ID credentials to access more ‘features’.
What makes AppDeceiver so dangerous is it’s not under MDM solutions’ control. Because the attack occurs at the network level, EMM solutions as well as app-only security solutions are blind to it. Network visibility is required in order for a security solution to be effective in preventing an iOS attack such as this one.
Safari Java scareware
 Type: Fake-Ransomware
Type: Fake-Ransomware
Severity: 29
Prevalence: 84
This type of malware has been perpetrated by scammers exploiting a vulnerability in the Safari mobile application on iOS devices. The vulnerability is related to how the Safari app handles JavaScript pop-ups. Attackers exploit this weakness using domains ridden with malicious code to target iOS end users.
If individuals visit one of these domains in their browser, either by navigating there on their own or being targeted by a phishing attack, the malicious code in the pages generate an endless loop of pop ups.
Safari, not beingable to cope with the mass number of pop-up screens, then locks users out of the application. The malicious code embedded in the page however, shows users a threatening ‘ransomware-esque’ message on the browser screen, demanding they pay a certain amount of money in the form of an iTunes gift card. The message suggests they must do this in order to to get the functionality of the device back.
The notification of course is bogus, as the scareware can’t function outside of the Safari sandbox and doesn’t have an impact on the rest of the device. In fact, the solution to get rid of this scareware is simply to navigate to the settings of the device and clear the ‘cache’.
Users have however, bought into the rouse, with many making the payments to the hackers. The clever social engineering of the webpage makes the threat believable to many. Some messages seem to come from the ‘UK police’ and accuse users of looking at pornography on their devices. The fee is positioned as a ‘penalty’ for their heinous actions.
While this specific fake-ransomware attack isn’t inherently dangerous to the device, it goes to show that iOS users can be easily targeted, even using the simplest of scams. These types of attacks can result in substantial financial losses.
iOS has since updated their OS to repair the Safari vulnerability, however as most of you know, many fail to keep their OS updated and are therefore still at risk.
XAgent
 Type: Spyware
Type: Spyware
Severity: 92
Prevalence: 17
This spyware variant targeting Apple iOS mobile users was uncovered being used by an active cyber espionage operation. This operation targets a wide range of entities such as large organizations, governments, defense industries and the media.
The spyware takes the form of a malicious application called XAgent. Once it is downloaded to the device, it runs in the background of the phone, not making itself apparent. If someone attempts to stop the download, it will simply restart.
This app is designed, as most spyware is, to capture information from the device. It can carry out multiple functions including, collecting text messages, acquiring contacts, viewing pictures, gaining geo-location data, starting a voice recording and getting a list of installed apps.
Once it collects this information, it sends it (via a C&C connection) back to the malicious server. This traffic travels over-the-air using the HTTP channel. This means that not only is the malicious hacker gaining access to this information, but any other third party on the network can view the data in plaintext.
It’s currently unknown how XAgent makes its way onto devices, however it is expected that social engineering is heavily involved in the process. In order for the malicious app to be downloaded, the iOS device must be jailbroken. To provide context, published research based on Wandera’s global network of devices shows that 1 in every 100 corporate devices has evidence of a jailbreak.
Pegasus
 Spyware
Spyware
Severity: 96
Prevalence: 9
Unless you’ve been living off the grid, you’ve likely heard the name Pegasus as the token example of iOS malware. Pegasus was the result of three specific zero-day iOS vulnerabilities that were exploited by attackers. It is a sophisticated spyware targeting iOS devices exclusively.
The malware is said to have been developed by an Israeli based organization that was acquired by a U.S. company in 2010. According to media reports, the business specializes in cyber-war. Pegasus was created to target high-level political dissidents and ‘enemies of the government’, but has since expanded its scope to a variety of valuable targets.
The anatomy of the attack is a classic phishing model. The victim is sent a text message with a link. If they click on the link, they are directed to a web page that immediately triggers the download of the spyware. The spyware proceeds to exploit the iOS vulnerabilities and gather information on the user, sending it back to the attackers through a C&C connection.
Of course, as is the case with most malware, it happens silently without the user’s knowledge. Pegasus targets all aspects of the device, even pulling information from apps such as Gmail, Facebook, Skype, WhatsApp, Viber, FaceTime, Calendar, WeChat, Tango, and many others.
Once downloaded, Pegasus is exceptionally difficult to remove, even when the device’s OS is updated. It’s almost never discovered as users tend to have no idea it was installed in the first place.
Now that the vulnerabilities in iOS have been patched, it’s of the utmost importance that users keep their OS up to date so as not to be affected by them.
Pegasus is an example of enterprise-grade malware that is specifically designed to target high-value individuals. The highly targeted nature of these attacks means that C-level executives are especially vulnerable.
It’s important to note MDM and app-only security solutions have no visibility at the network level where these phishing attacks, like this one, take place. They can therefore, not sound the alarm on Pegasus, or block its malicious traffic before it hits the device.
The moral of the story
Based on the above examples, you can clearly see that malware is not an Android-only problem. It is fair to say that Android is subject to more instances of malicious malware thanks to its open OS, however, there have been multiple zero-day exploits that have exclusively affected iOS.
How Wandera can help
 This analysis has made clear that visibility at the device, network and data levels is absolutely paramount when it comes to detecting iOS malware. Wandera is the only solution with a web gateway for mobile that allows it to detect threats at all levels, differentiating it from any EMM or app-only security solution. Thanks to its ability to sit directly in the path of data, Wandera can actually intercept and block threats before they reach the device.
This analysis has made clear that visibility at the device, network and data levels is absolutely paramount when it comes to detecting iOS malware. Wandera is the only solution with a web gateway for mobile that allows it to detect threats at all levels, differentiating it from any EMM or app-only security solution. Thanks to its ability to sit directly in the path of data, Wandera can actually intercept and block threats before they reach the device.
In addition, Wandera alerts admins when users haven’t updated their OS as well as when apps are sideloaded to the device. This gives IT teams unprecedented visibility into vulnerabilities that could result in malware infiltration, allowing them to proactively protect the fleet.
To ensure your iOS devices remain as safe as they’re thought to be, make an appointment with one of our mobility specialists now. When the next wave of iOS malware hits, you’ll be glad you did.








